Report: DDoS attacks surge
January 24, 2024

Gcore, a cloud and edge solutions provider, has revealed the findings of its Q3-Q4 2023 Gcore Radar report that provides insights into the current state of the DDoS protection market and cybersecurity trends.
The report finds that there were a number of significant developments in the scale and sophistication of cyberthreats in H2 2023.
Key Highlights from Q3–Q4
- The maximum attack power rose from 800 Gbps (1H 2023) to 1.6 Tbps.
- UDP floods constitute 62 per cent of DDoS attacks. TCP floods and ICMP attacks remain popular at 16 per cent and 12 per cent respectively and SYN, SYN+ACK flood, and RST Flood, account for just 10 per cent combined.
- The most-attacked business sectors were gaming (46 per cent), financial (including banks and gambling services) (22 per cent) and telecom (18 per cent).
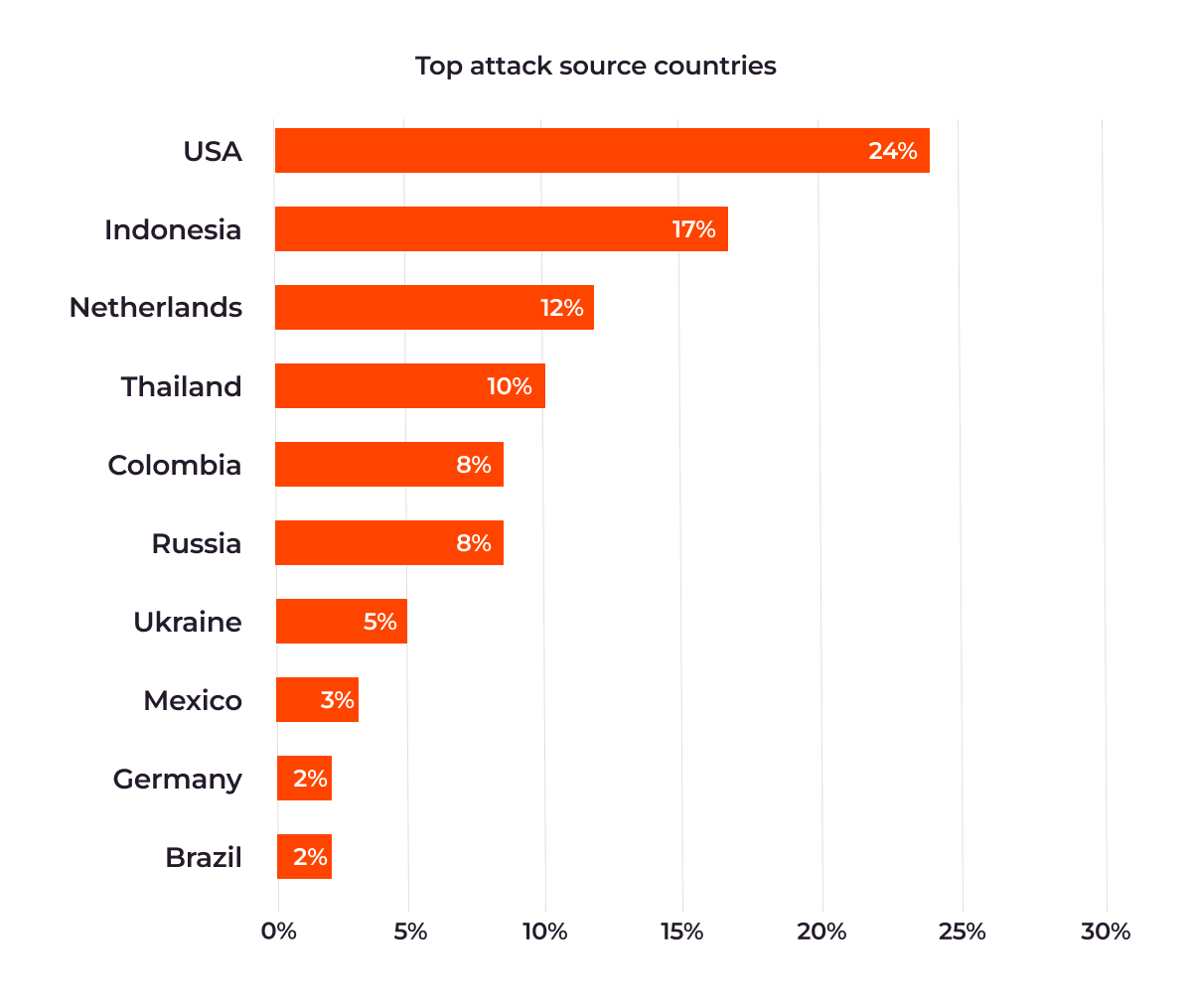
- USA (24 per cent), Indonesia (17 per cent) and The Netherlands (12 per cent) list as the top three attack source countries.
- In Q3/Q4, the longest attack duration lasted 9 hours.
- The average length of attack was approximately an hour.
High-Volume Attacks: A Surging Threat
The past three years have brought about a >100 per cent annual increase in DDoS peak (registered maximum) attack volume:
- In 2022, the peak capacity of DDoS attacks increased from 300Gbps (2021) to 650 Gbps
- In Q1–Q2 of 2023, it increased again to 800 Gbps
- In Q3–Q4 of 2023, it rocketed to 1600 Gbps (1.6 Tbps)
The jump in H2 of 2023 has resulted in the cybersecurity industry now measuring DDoS attacks in a new unit, Terabits. This escalation illustrates a significant and ongoing rise in the potential damage of DDoS attacks which, according to Gcore, is a trend that it expects to see continue in 2024.
DDoS Attack Techniques
According to Gcore’s statistics, in Q3-Q4 of 2023:
- UDP floods continue to dominate having become more popular amongst attackers in H1 of 2023.
- TCP floods and ICMP attacks have jumped into second and third place respectively.
- There was a decrease in the number of SYN flood attacks from 24 per cent in H1 of 2023, seeing SYN, SYN+ACK floods, and RST Floods making up the remaining types of attack in Q3/Q4.
Commenting on these findings, Andrey Slastenov, Head of Security Department at Gcore, said: “The exponential surge in attack power and variation in attack methods that we saw in the second half of 2023 illustrates how sophisticated cyber attackers are becoming. It’s more essential than ever for organisations to adopt a multifaceted defence strategy that can protect against a range of DDoS techniques. Failure to address these evolving threats can result in costly disruptions, reputational damage, loss of customer trust, and security breaches.”
DDoS Attacks by Geography
Gcore’s findings in the latter half of 2023 illustrate a widespread global threat as it identified attack sources ranging from the US, Indonesia and The Netherlands as the top three countries respectively, and Mexico, Germany and Brazil coming in as the bottom three attack source countries.
DDoS Attacks by Business Sector
According to Gcore’s report, the gaming, financial and telecom were the most attacked sectors in Q3–Q4 of 2023 which is likely to be due to their financial gains and the potential impact on users. These findings underscore the need for targeted cybersecurity strategies like countermeasures for specific gaming servers.
Slastenov concluded: “The increase in attack power to 1.6 Tbps is particularly alarming, signalling a new level of threat for which organisations must prepare. Paired with the geographical distribution of attack sources, it’s clear that DDoS threats are a serious and global issue, necessitating international cooperation and intelligence sharing to mitigate potentially devastating attacks effectively.”
